Organizations have been scampering to protect data, identities, and other digital assets from Cyber Attacks. AI has further strengthened the hand of Cybercriminals, enabling them to unleash a new generation of threats. Cybercriminals are using ML to improve algorithms for guessing passwords using AI/ML ability to quickly analyze large password data sets. On the other hand, Cybercriminals can use Deepfakes to spread political or societal misinformation or even craft non-consensual porn of unwilling people. AI algorithms can analyze communications and craft convincing phishing emails to deceive recipients into disclosing sensitive information or initiating fraudulent transactions. AI can automate and enhance ransomware to target valuable assets. AI can be leveraged to evade security measures and exploit vulnerabilities in the business system.
The future evens out the advantages by pitting machine against machine. AI in cybersecurity is being used to detect what is normal business functioning and spot any deviations in real-time to enable quick response and improve the overall accuracy and efficiency of defense against cyber attacks. Going beyond the dated conventional approach of detecting threats based on signatures, AI in cybersecurity solutions identify behavioral patterns such as using specific ports at a particular time, a sudden surge in data download, and specific patterns or anomalies to detect an incident and take action before substantial damage is caused.
Thus, AI in cybersecurity offers the benefits of faster threat detection, proactive response, and greater scalability by evaluating network traffic patterns, analyzing large amounts of data to identify potential threats that may not be immediately apparent to humans, automating routine monitoring and reporting tasks, and reducing cybersecurity costs. AI can manage large and complex networks with ease. By incorporating AI in cybersecurity strategies, businesses can augment their security measures and work with a higher degree of confidence.
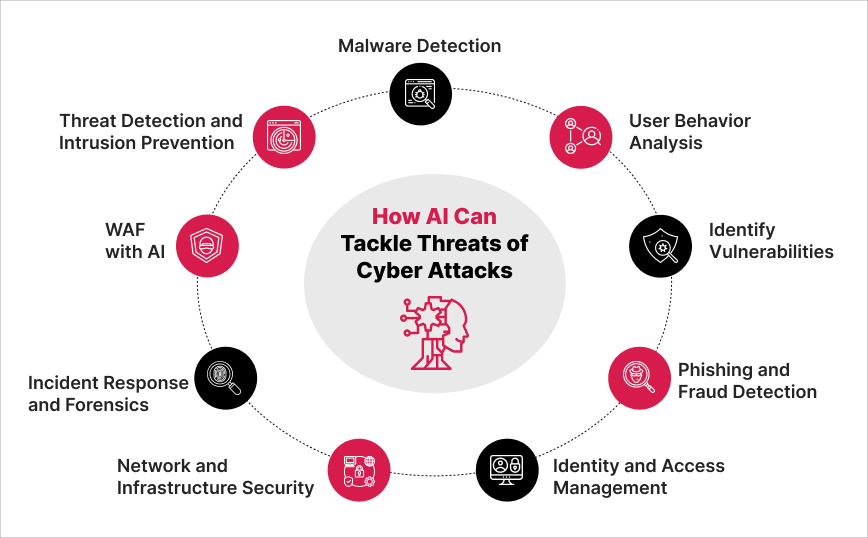
How AI Can Tackle Threats of Cyber Attacks
AI in cybersecurity has emerged as a valuable tool to combat the ever-evolving sophistication of complex cyber threats. AI is being smartly deployed to counter cyber attacks. AI is being used to automate the deployment of deception technology to misdirect attackers or lure them into a trap. Some of the ways in which AI in cybersecurity helps stay a step ahead are:
#1. Threat Detection and Intrusion Prevention
AI and deep learning algorithms quickly analyze enormous amounts of data and patterns to uncover potential threats and detect anomalies in network traffic or user behavior. Using Artificial Intelligence in cybersecurity, organizations can transition from the traditional methods that rely on administrators to specify good or bad application traffic.
Unsupervised deep learning algorithms can develop a positive security model of your application in real-time to promptly identify and respond to cyber threats. This proactive approach allows for prompt detection and response to cyber threats, making AI in cybersecurity an invaluable tool for safeguarding against evolving risks.
#2. Malware Detection
Detection and Prevention based on signatures are reactionary and cannot contain the initial damage that malware can cause. With AI in cybersecurity, the approach is to detect and classify malware by analyzing behavioral patterns, code patterns, and file characteristics. Supervised deep learning can train multiple models with large data sets and apply the trained models to detect malware behavior and identify new and evolving malware variants.
Using deep learning algorithms to model malware activities can sometimes result in false positives and false negative misclassifications. It may misclassify malware activity as benign—a false negative, or benign activity as malware—a false positive. Combining the modeling of both bad and good behavior can improve the success rate. This switch from trapping (based on signatures) to hunting (based on modeling behavior) tried to detect sudden excessive use of computing resources by monitoring abnormal requests, connection requests from non-validated sources, the abnormally high quantum of data getting transferred externally, typical requests coming in at atypical times, and so on.
ML is ideal for anti-malware protection since it can draw on data from previously detected malware to detect new variants, including identifying covert channels and file-in-file activities. While hunting requires substantial computing resources and continuous and ongoing improvement, it is the best approach for proactive defense.
#3. User Behavior Analysis
Threats extend beyond external sources, encompassing internal risks as well. However, Artificial Intelligence in cybersecurity can address such challenges effectively. AI models can be set up to determine standard user patterns and quickly identify any deviations. Computing enables round-the-clock monitoring of any such suspicious behavior and mitigates insider threats.
#4. Identify Vulnerabilities
Every organization digitally stores sensitive data, such as financial, personal, customer, and similar information, which is constantly under cyber threat. Today, various vulnerability scanners come equipped with comprehensive automated tests. These tests are designed to efficiently scan and analyze systems, applications, and networks to pinpoint potential vulnerabilities attackers can exploit. AI models rank these vulnerabilities in the order of risk they pose to enable prioritized mitigation.
#5. Phishing and Fraud Detection
AI models effectively analyze email content, URLs, and other characteristics to recognize and flag abnormal patterns for removal. Also, AI models analyze vast piles of historical data to recognize patterns and undergo continuous improvement by analyzing real-time data to stay a step ahead of phishing attacks, which are getting more sophisticated by the day.
#6. Identity and Access Management
Simple algorithms have helped gauge password strength and encourage users to have a stronger password. Multifactor authentication is already the norm in most places. Today, algorithms can detect compromised credentials by analyzing various factors, such as user behavior, the location of access requests, and the characteristics of the devices used to access the account. By considering all these factors, the algorithms can determine the authenticity of the access requests and prompt additional information if any suspicious activity is detected.
AI in cybersecurity strengthens the security layer by using tools like facial recognition and fingerprint scanners to secure authentication during login attempts and prevent credential stuffing and brute-force attacks.
#7. Network and Infrastructure Security
A behavior-oriented approach can be deployed to analyze network traffic patterns, detect unusual activities, and identify potential attacks like distributed denial-of-service (DDoS) attacks or intrusion attempts.
#8. Incident Response and Forensics
Artificial Intelligence in cybersecurity can aid in automating incident response processes by analyzing and correlating security event data, identifying the root cause of incidents, and suggesting remediation actions. It can also assist in digital forensics investigations by processing large volumes of data and uncovering hidden patterns.
#9. WAF with AI
WAFs are increasingly becoming part of the application security strategy. Web applications and API protection (WAAP) provide security from the edge of the database.
Use of AI in Cybercrime
With rapid technological advancements, such as AI in cybersecurity, organizations need to navigate the ever-changing environment. However, it poses various challenges for businesses in their pursuit of ensuring the security of their systems and data. Here are some key challenges:
#1. Cloud Adoption
Organizations are leveraging multiple cloud providers for their business needs. While it offers flexibility, it also attracts complexity. It increases the number of platforms and interaction points an application has to provide consistency across, ensuring it does not create an increasing number of vulnerabilities.
#2. API Integrations
The integration of systems and services through APIs has become prevalent. However, this also makes APIs a prime target for hackers. Therefore, protecting data ‘in transit’ and ‘in use’ has become a significant concern for organizations.
#3. AI in Cyber Attacks
Artificial intelligence (AI) and machine learning (ML) methods are increasingly adopted in cyber attacks. AI supports the establishment of covert channels to siphon sensitive information. Therefore, these technologies enable cyber attackers to enhance their methods and tactics, making it more challenging for traditional security measures to spot and prevent their activities.
#4. AI in Malware
Malware creators increasingly deploy AI and ML methods to enhance the capabilities of their attacks. They can incorporate new, sophisticated, and changing features and functions on the fly, creating AI-driven malware that can continually adapt and evade traditional defense mechanisms. Therefore, AI in cybersecurity will play a vital role to combat these scenarios.
#5. AI-Driven Threats
The evolving environment presents a host of other threats that gain momentum by leveraging AI. These include targeted attacks against AI detection functions, advanced payload obfuscation techniques, evasion of networked communication with AI methods, decentralized botnet control using swarm intelligence, and the concealment of malware payloads within neural networks.
How Robosoft Helps Build an Environment of Trust
Robosoft helps its customers tackle cyber threats through two approaches:
- Risk-based Approach: The National Institute of Standards and Technology (NIST) adopts a risk-oriented approach to reduce cybersecurity risks to networks and data. Domain-specific frameworks such as HIPAA or standards such as PCI/DSS are woven into the approach.
- Compliance-based Approach: Frameworks such as ISO 27001 list 14 security control areas and 114 controls against which projects can be deployed to build an effective shield against threats and be security compliant.
At Robosoft, we provide a wide range of cybersecurity services to address security challenges. We help assess:
- Environment Risk, Cybersecurity Maturity, and Security Architecture
- Formulate operating policies and procedures.
- Evaluate security vendors and tools.
- Program management of the cybersecurity program
In addition, Robosoft helps deploy the selected tool across the complex organizational landscape. We specialize in identifying security tools that provide spherical (not just 360°) security and deploying them to keep threats at bay and meet compliance requirements.
Furthermore, Robosoft has a systematic methodology for each area of security and an overarching security program.
The Future of AI in Cybersecurity
At Robosoft, we believe AI is here to become an intrinsic part of cybersecurity, ushering in a transformative era. As the landscape of digital threats becomes increasingly complex and insidious, our vision for the future of AI in cybersecurity embodies a significant change from a reactive approach to a proactive one.
Traditionally, cybersecurity played a follower role through a reactionary force in post-attack solution development. However, as we progress to behavior and pattern-based defense, particularly through the use of AI in cybersecurity, security solutions will be able to steal a march over threats, enabling faster and more accurate responses to cyber threats.
- Authentication techniques will get more sophisticated, incorporating facial detection, biometrics, and such solutions along with behavioral analysis and anomaly detection.
- Vulnerability detection will not be limited to just scanning and identifying weaknesses but will include real-time remediation.
- Continuous monitoring and analysis of vast amounts of data will enhance the Intelligence of Intrusion Detection Systems (IDS) by incorporating behavior and pattern-based approaches. It will enable them to adapt to emerging threats and significantly improve their response accuracy and speed.
- Adversarial AI will be leveraged to feed manipulated data to malicious actors that, too, leverage AI to launch sophisticated attacks, thereby evading detection. Nevertheless, machine learning algorithms will continuously evolve to counter such AI-based threats.
Security threats will persist and get more sophisticated over time. With AI in cybersecurity, we have an effective countermeasure against such threats.