In today’s digital world, protecting your content goes beyond just security—it’s about keeping your business model safe, meeting content license rules, and boosting customer satisfaction. Getting a handle on DRM video protection is key for businesses looking to shield their revenue, stick to content agreements, and give customers a top-notch experience with Digital Rights Management (DRM).
Protecting streaming video content with DRM
DRM-protected videos are encrypted and packaged using multiple DRM schemes for cross-device compatibility. Upon playback initiation, the video player requests a decryption key from a license server, which verifies user and device authorization. Upon successful verification, the server issues a license response containing the decryption key, enabling the player to decrypt and play the content. Platforms typically embed a DRM mechanism in hardware or the operating system, though third-party vendors can also create DRM software.
DRM encrypts and packages digital assets, ensuring that content retains value and is only accessible to those who have rightfully paid for it.
The DRM process generally involves the following steps:
- Digital assets are encrypted (part of the “packaging” process) and are unlocked only by a secret encryption key. Think of encryption as putting your video in a safe. Only those with the right combination can open it.
- The encryption key is bundled with a digital license that specifies content usage rules. A license server is like a bouncer at a club. It checks if you have the right ‘ticket’ (license) before letting you in to enjoy the show.
- The DRM client checks the license upon a user’s content request (e.g., clicking to watch a show).
- If the license check passes, the user receives a validation token.
- This token authorizes the receiving device to decrypt the content.
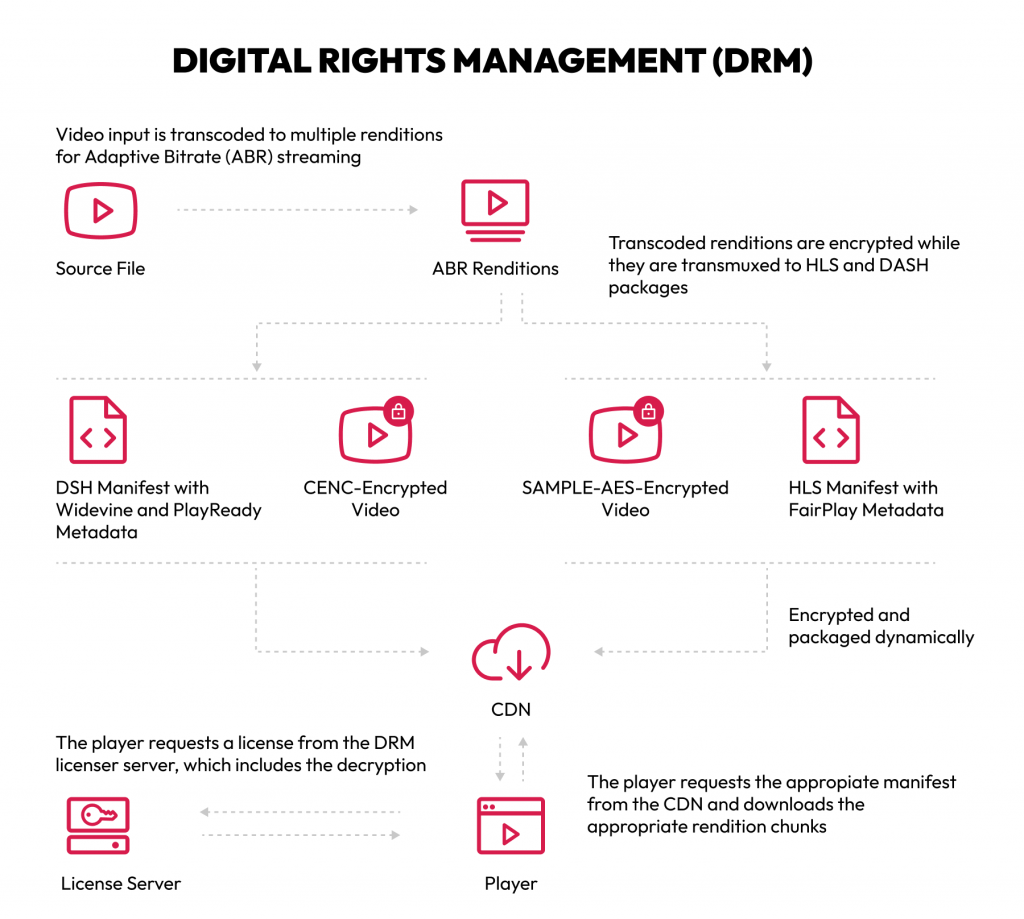
The image above illustrates the DRM process, from transcoding and encryption to delivery and playback, showing how content is secured and accessed across different systems.
Content packaging for DRM
- Content encryption and packaging:
- DRM requires content to be encrypted and packaged in formats like MPEG-DASH, HLS, or Smooth Streaming to prevent unauthorized use.
- This can be done during transcoding or post-transcoding.
- Some platforms and CDNs offer just-in-time encryption and packaging, allowing content protection without the need for re-transcoding upon player request.
- DRM systems compatibility:
FairPlay, Widevine, and PlayReady are leading DRM systems developed by Apple, Google, and Microsoft, respectively, each designed to secure video content by encrypting it and managing access across different devices and platforms.
- Widevine and PlayReady: Support Common Encryption (CENC) and use MPEG-DASH, allowing for a single encryption and packaging process.
- FairPlay: Uses Sample-AES encryption with HLS packaging, necessitating separate encryption and packaging for full three-system support.
- DRM video requirements:
- Each DRM-protected video typically involves encryption keys and identifiers, though specific requirements may vary by platform or DRM system.
- Both CENC and FairPlay use AES 128-bit keys for encrypting content.
- FairPlay also requires an initialization vector (IV).
- These keys and IDs can be manually generated or automatically created using license server tools.
- Key and ID management:
- Keys and IDs are ingested into the license server for delivery to the player to decrypt content.
- Secure storage of these keys within the platform is vital for backups and transitions to new license servers.
Delivering protected content
The following technologies facilitate DRM-protected content delivery to a wide range of browsers and devices:
- MPEG-DASH with native/EME-supported CENC DRMs
- HLS with FairPlay, Widevine, and PlayReady
Ensuring your player works with DRM means you can offer a seamless viewing experience, keeping your customers happy.
Content creators and owners may also choose to enforce HDCP for specific hardware configurations. A fallback mechanism providing lower-quality SD playback is necessary for devices lacking HDCP support.
Why implement DRM video protection?
While some streaming protocols offer encryption (e.g., HLSe), this alone is insufficient for robust video content protection. DRM, which utilizes a secret encryption key, presents a significantly greater challenge to circumvention.
- Revenue protection: DRM ensures that your content, like exclusive movies or training videos, isn’t freely distributed, protecting your revenue streams from piracy. This is crucial for subscription-based models or pay-per-view events. For instance, Netflix uses DRM to ensure that only subscribers can watch its content. When you stream a movie, your device communicates with Netflix’s servers to verify you have a valid subscription (like a ticket). Only then does the server give your device the key to unlock the video, ensuring that sharing an account for movies outside the household is challenging.
- Compliance: Many content agreements require DRM to prevent unauthorized sharing. Failing to comply can mean losing access to valuable content or facing legal repercussions. YouTube, for example, employs DRM for its Premium service, where certain features like offline downloads or ad-free viewing are locked behind this digital security. When you download a video for offline viewing, it’s encrypted. Your device must re-verify your Premium status each time you want to watch it, ensuring that only paying subscribers enjoy these benefits.
- Content control: By controlling distribution, you’re securing your content and tailoring your business model, enhancing customer loyalty through exclusivity. Many media companies use DRM to:
- Limit concurrent device access, preventing account sharing.
- Enable the creation of ‘exclusive content’ offerings, enhancing perceived value.
- Detect jailbroken or rooted devices, adding an extra layer of security.
- Prevent screen recording or screenshots, protecting content integrity.
- Combine with proxy/VPN detection to block unauthorized access.
- Support offline content protection, allowing users to download content for viewing without internet access while preventing sharing.
Implementing DRM: a three-part process
Implementing DRM video requires modifications to at least three components of your streaming workflow:
- Content preparation: Assets must be transcoded, encrypted, and packaged in formats compatible with the target DRM technologies.
- Player integration: The video player must request decryption keys from a license server and decrypt the video. This may necessitate different players across platforms.
- License server integration: The video player requests decryption keys from a license server for each content request. Typically, publishers integrate with multi-DRM license service providers like Axinom or EZDRM rather than setting up their own servers. The license server authenticates these requests and provides responses.
Businesses like Netflix and YouTube have leveraged DRM to protect their content, offer different viewing options, secure their business models, and maintain a competitive edge in the streaming market.
Challenges of video DRM
Understanding and evaluating potential drawbacks associated with this technology is essential before researching platform options and DRM integrations.
- Viewer experience: Increased security inevitably introduces more potential points of failure during playback. For example, license requests may experience delays or timeouts, potentially causing latency or video abandonment.
- Compatibility: A single DRM schema does not exist for every device, platform, and browser. Therefore, DRM videos require transcoding with multiple schemas. While leading systems cover a significant portion of the digital landscape, some lower-resolution devices may remain incompatible.
- Cost considerations for publishers: Beyond end-user challenges, DRM integration involves significant costs, including license key delivery fees from multi-DRM service providers, infrastructure setup, and ongoing maintenance.
Additional content protection security layers
Beyond DRM, other security measures can further protect content:
- Encryption: Full DRM or AES-128 (HLSe) protection.
- License Key Protection (LKP) safeguards decryption keys from unauthorized access, whether for DRM- or AES-128-protected content.
- Platform-based quality limiting: Dynamic delivery rules allow the specification of deliverable renditions by device type, limiting quality for devices that do not meet output protection requirements.
- Fallback HDCP: Each rendition uses a unique decryption key with its security configuration. This allows players to select compatible renditions and ignore incompatible ones. For example, a device user unable to support Widevine Level 1 will experience SD quality playback, with HD renditions (protected by HDCP) unavailable.
- Forensic watermarking: This feature embeds an invisible watermark into the video, enabling content owners to quickly identify the source of content leaks, strengthening confidentiality and intellectual property protection.
Protecting your digital content with DRM isn’t just about technology; it’s about securing your business model, meeting legal standards, and ensuring your customers receive the expected value. Implementing robust DRM is crucial for safeguarding premium video content in today’s streaming landscape. A technology partner like Robosoft can help you navigate the complexities of DRM encryption, ensuring content security and protecting against piracy and unauthorized access. We support integration services with the market’s leading players for DRM encryption. Contact us today to discuss your DRM strategy.